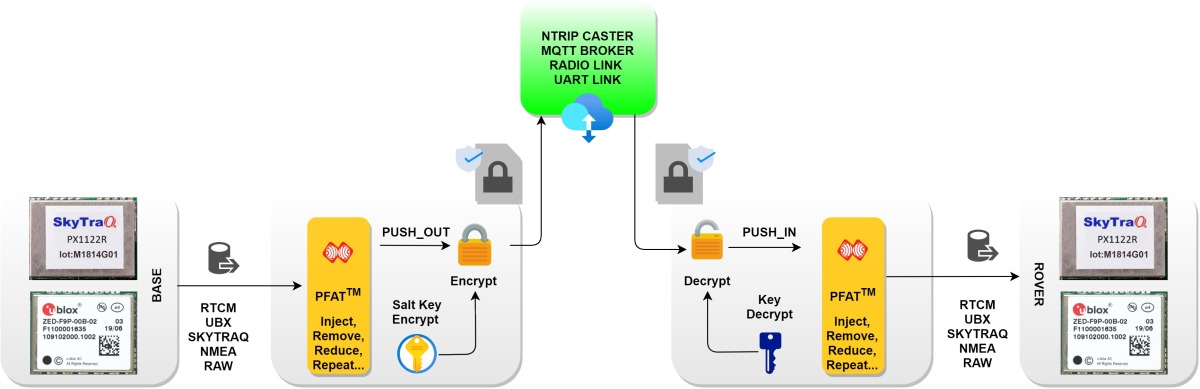
Encrypt and Decrypt to protect private stream data .
Starting with version 3.9.91, we have supported the feature that allows ESPrtk to encrypt data that runs through the stream.
When the data is encrypted, this means that all the information inside the data will be scrambled, jammed... Only devices with the decryption key can restore the data to its original state. .
In this way, the RTCM/UBX/SKYTRAQ/RAW ... data flowing through the stream will be protected (the content cannot be read and analyzed/parsing if encrypted).
Using this feature will also allow users to commercialize RTCM data from the RTK BASE station (PUSH_OUT) by managing/distributing/selling decryption keys to ROVER side users (PUSH_IN).
ESPrtk supports AES_128 and AES_256 encryption algorithms. (A form of the most powerful and secure algorithm available today, it takes 1000 million years to decrypt by Brute-force attack method if you want to crack it!).
ESPrtk supports 3 types of configuration:
- Encrypt output data only.
- Decrypt input data only.
- Decrypt input data and encrypt output data at the same time.
On ESPrtk 3.9.91, This feature supports on threads running through the following types of main actions:
- MQTT RTK Basestation
- MQTT RTK Rover
- NTRIP RTK CASTER Server
- NTRIP RTK Basestation
- NTRIP RTK Rover
- RADIO RTK Basestation
- RADIO RTK Rover
- UART Base to UART Rover bridge
Encrypt output data only.
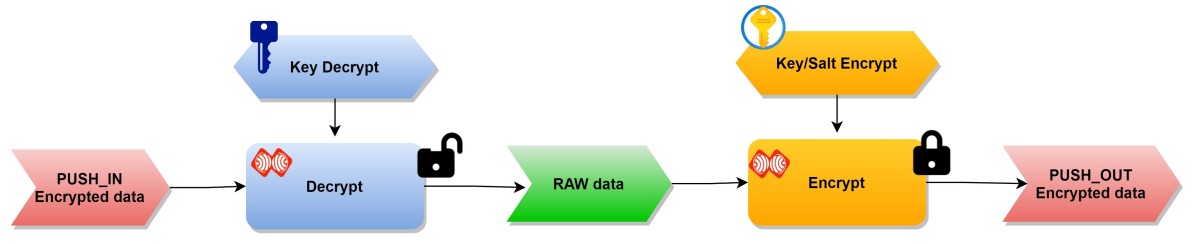
RTCM/UBX/SKYTRAQ/RAW data will be encrypted and encapsulated in ESPRTK encrypted message format before being push out (sent).
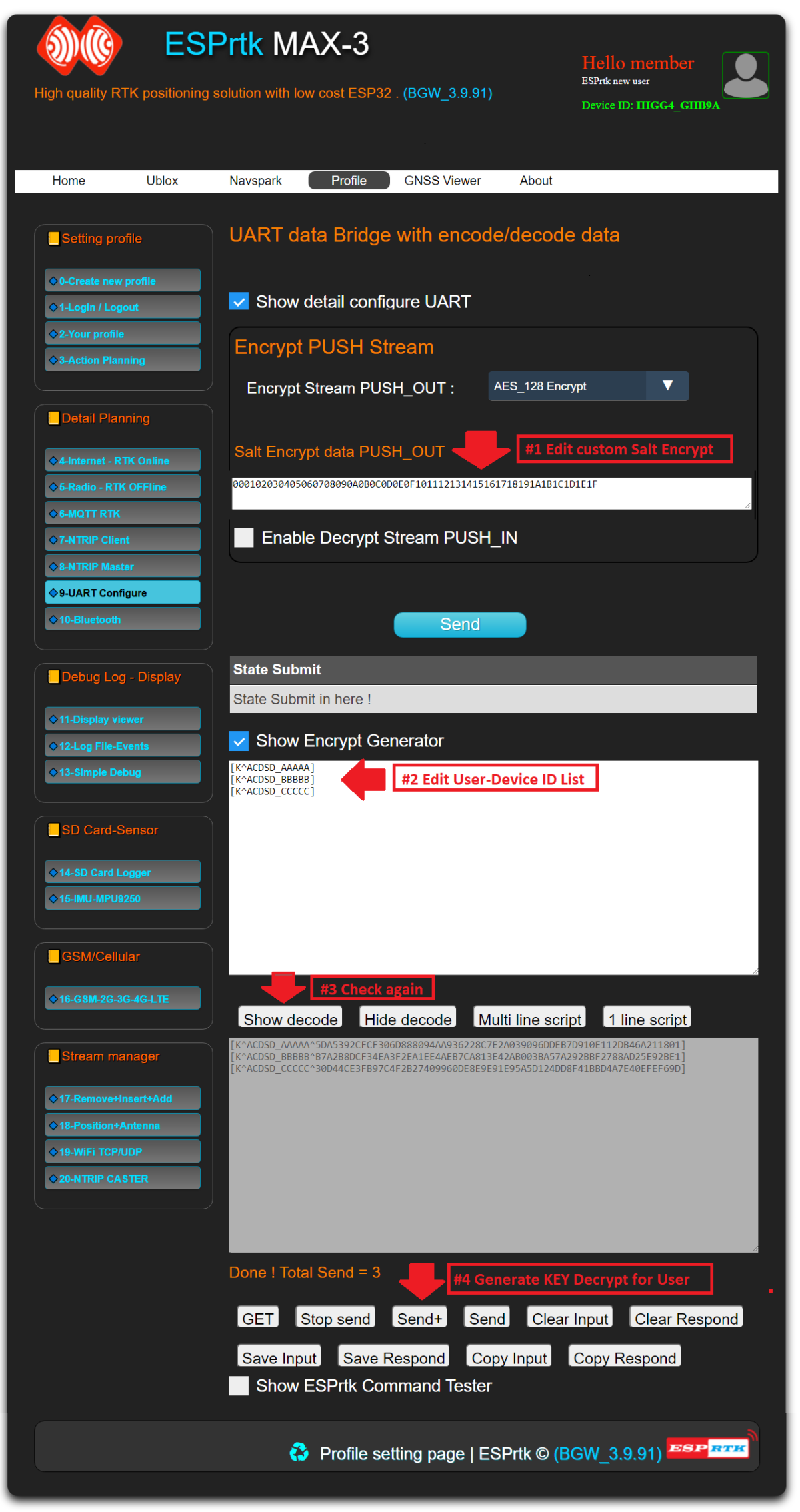
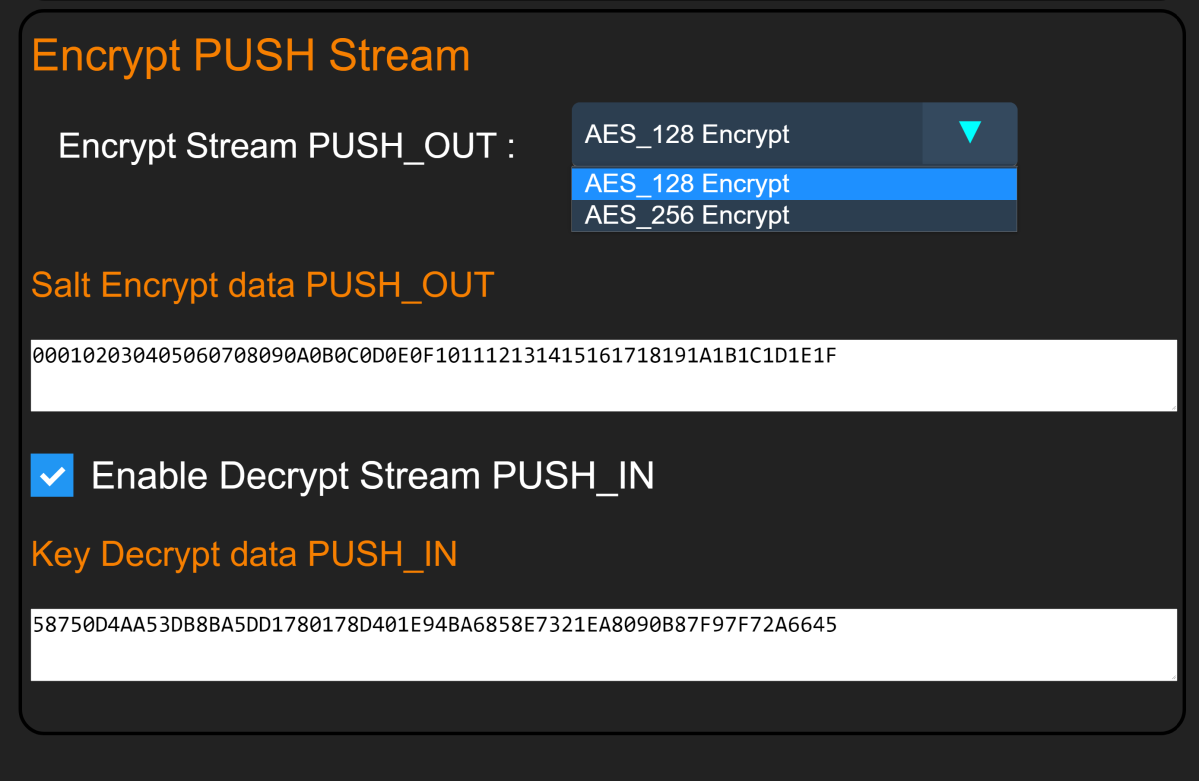
Enable this feature by selecting one of two encryption types, AES_128 or AES_256, in the drop-down menu of the UART_CONFIGURE tab page.
This feature requires providing a HEX 32 Byte length encryption key. (Salt)
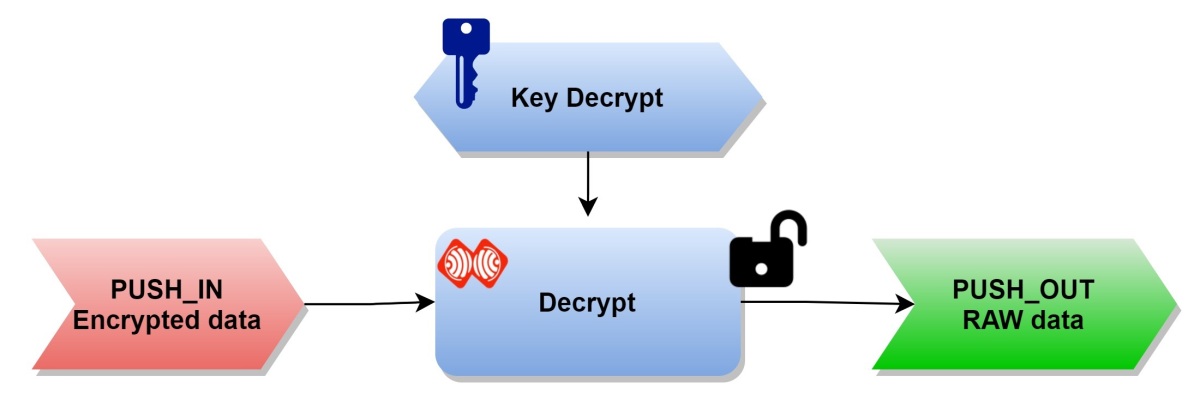
Decrypt input data only.
The input data is an encrypted message in ESPRTK format. This data will be decoded automatically before entering the FATP stream processor.
Enable this feature by enabling the "Decrypt Stream PUSH IN" flag in the UART_CONFIGURE tab. This feature requires providing a 32 Byte decryption key.
Each device has a decryption key corresponding to that device's ID. Since the ID on each device is different, the Decryption Key on each device is also different!
The decryption key is generated using the encryption key generator. Read detail in below .
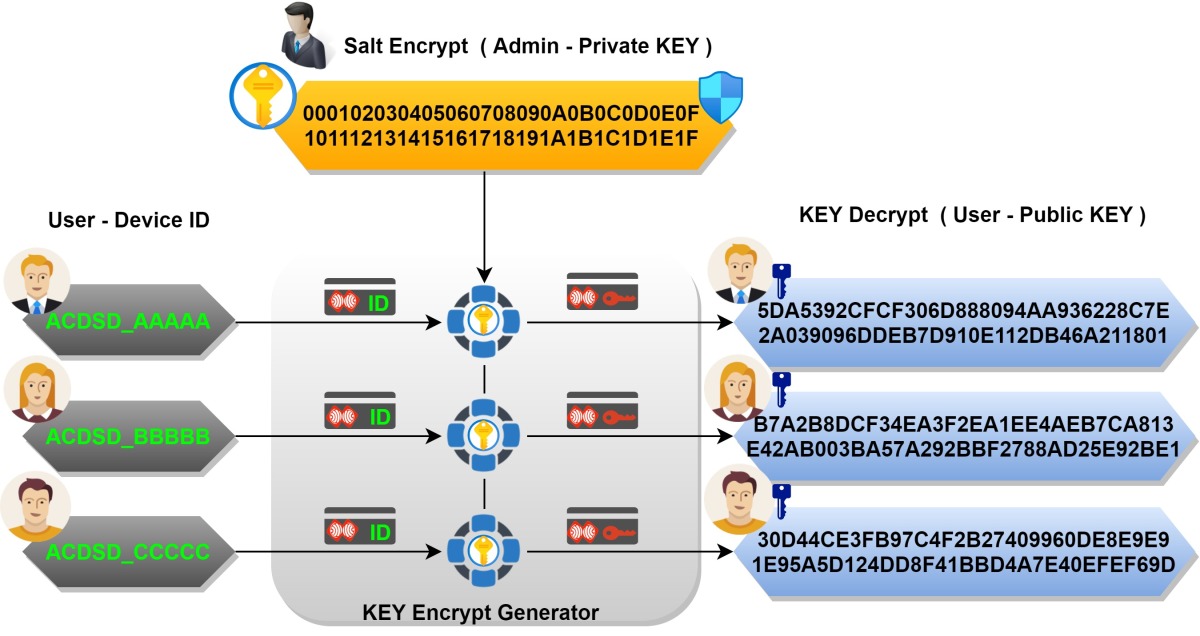
Encryption key generator.
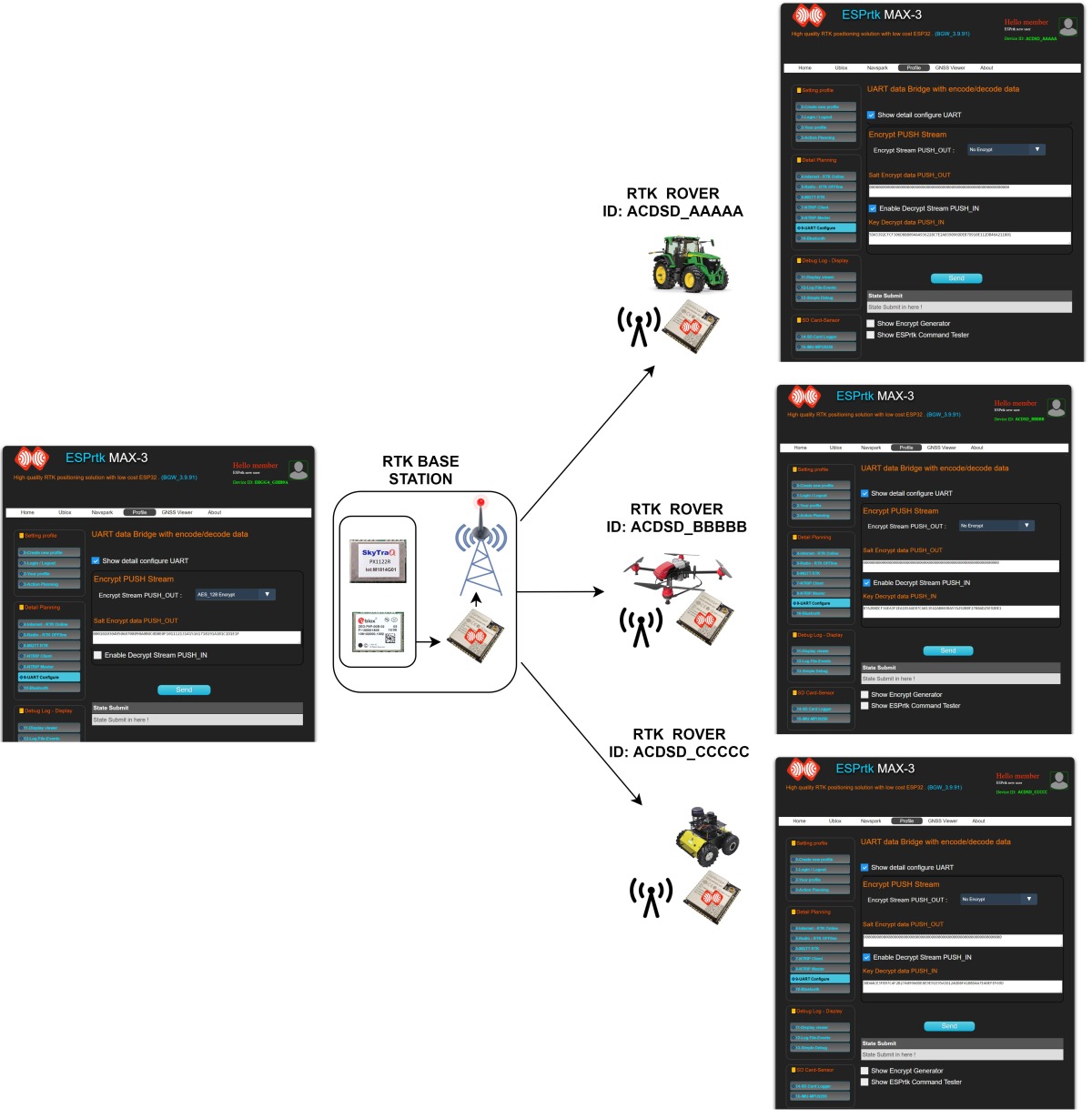
Let's start with an example for 1 BASE station and 3 Rover.
- For example, the ID of each Rover in turn is:
- + ID-Rover A : ACDSD_AAAAA
- + ID-Rover B : ACDSD_BBBBB
- + ID-Rover C : ACDSD_CCCCC
We will build a BASE station to send RTCM data to the Rovers , and RTCM data needs to be encrypted to ensure data security (only Rover side users with valid decryption keys can recover encrypted RTCM data).
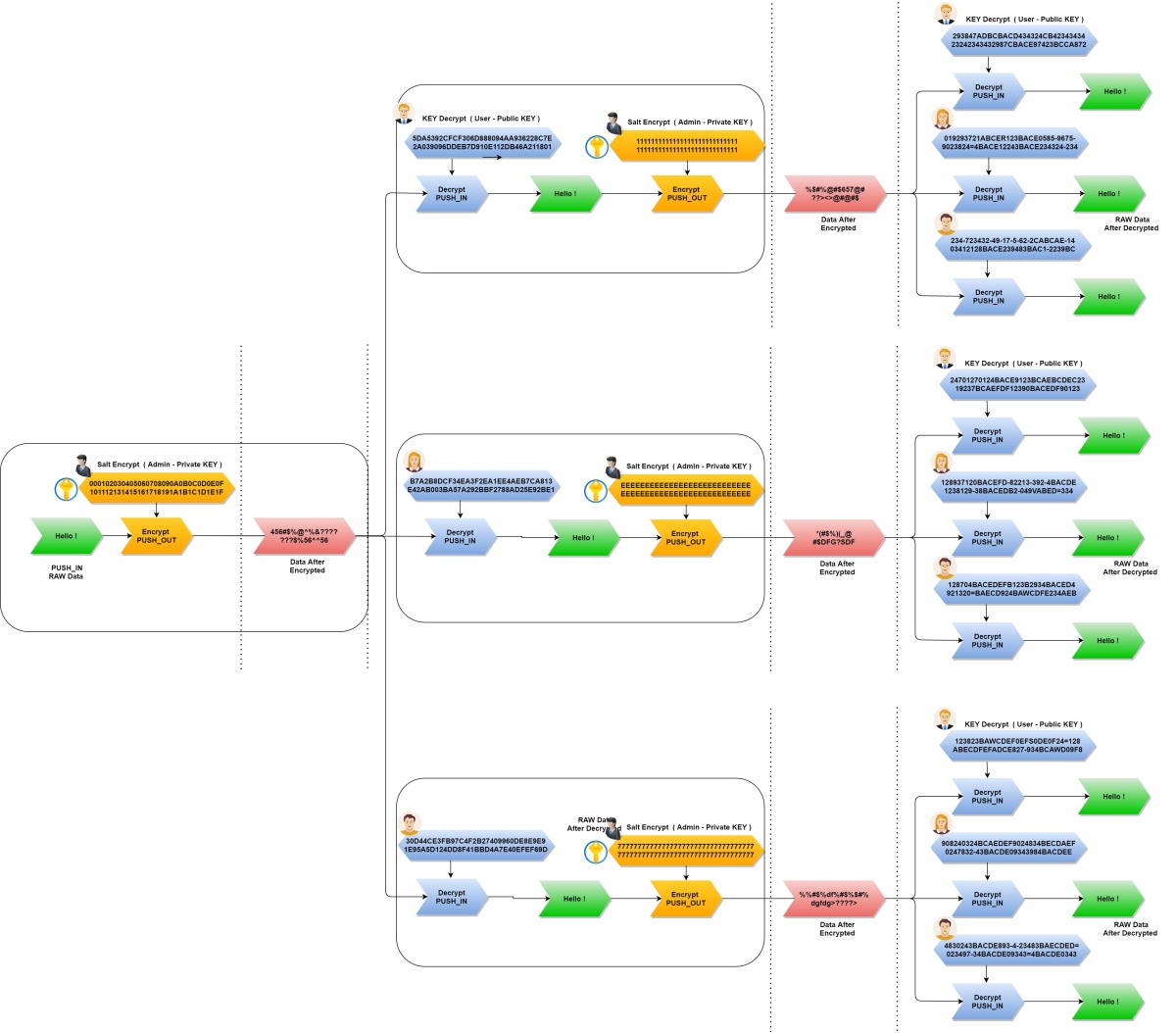
First, the Base station manager (Admin) will generate a 32 BYTE HEX string as the encryption key on the BASE side.
For example : 000102030405060708090A0B0C0D0E0F101112131415161718191A1B1C1D1E1F
Note: Admin does not share/disclosure this key string to anyone!
Then enter the input frame with 2 formats:
- Minimum : [K^_ID_]
- Full : [K^_ID_^^_Email_^_NAME_^_Tel1_^_Address1_^_Tel2_^_Address2_]
In this case, the input string would be:
Press the 'SEND+' button, we get 3 corresponding keys for 3 users.
- KEY-Rover A: 5DA5392CFCF306D888094AA936228C7E2A039096DDEB7D910E112DB46A211801
- KEY-Rover B: B7A2B8DCF34EA3F2EA1EE4AEB7CA813E42AB003BA57A292BBF2788AD25E92BE1
- KEY-Rover C: 30D44CE3FB97C4F2B27409960DE8E9E91E95A5D124DD8F41BBD4A7E40EFEF69D
These keys will then be provided to the user corresponding to the ID on their device.
Class hierarchy and key management.
Example to configure on Base and Rover .
- Image Configure for BASE
- Image Configure for ROVER-A
- Image Configure for ROVER-B
- Image Configure for ROVER-C
Decrypt input data and encrypt output data at the same time.
Is a combination of 2 functions Encryption and Decryption if enabled at the same time.
ESPrtk will simultaneously decrypt, parse and re-encrypt one more time.
This will allow the model to work with multilayer mode.
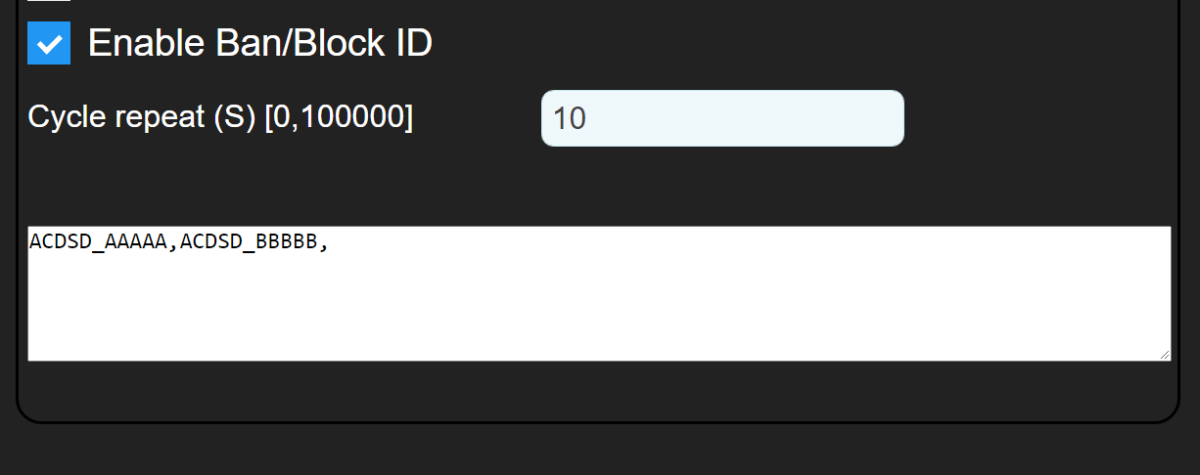
Ban or Block the device by ID.
You can block any user (device) without changing the encryption and decryption keys of the entire system.
Do this by adding the ID of the device the admin wants to block into the encrypted stream.
If there is more than 1 device, each ID will be separated by a comma.
On version 3.9.92, it is possible to block up to 100 IDs at a time.
Devices in the ID block list will not be able to decode the signal because it is blocked.
Devices that are NOT in the ID block list can decrypt data as usual.
Q/A.
What if the Rover user's Encryption key is disclosured?
As you can see, the decryption keys for each user are different and only valid on that device. The disclosure of a certain user's key on the Rover side will not affect the security of the remaining keys!
What if the Encryption key at the BASE station is disclosured?
It is not safe to disclosured the Encryption key at the BASE station! It is necessary to change the Encryption key at the BASE station again and generate new keys for the Rovers .